Wikileaks has once more released a series of documents that claim to show malware the CIA used to spy on owners of Apple products. And they are pretty hardcore. The CIA’s Target: Macs We have seen many examples of how the CIA, among other organizations, have used exploits to get […]
Tag: CIA
What you need to know about Wikileaks and CIA’s Hacking Program
Wikileaks have released a new batch of classified documents, this time from the CIA. Per the documents, the CIA have a section like the NSA, but with less accountability and oversight. The CIA’s Tools and Wikileak’s Vault 7 The new series of leaks is titled “Vault 7”, and the first […]
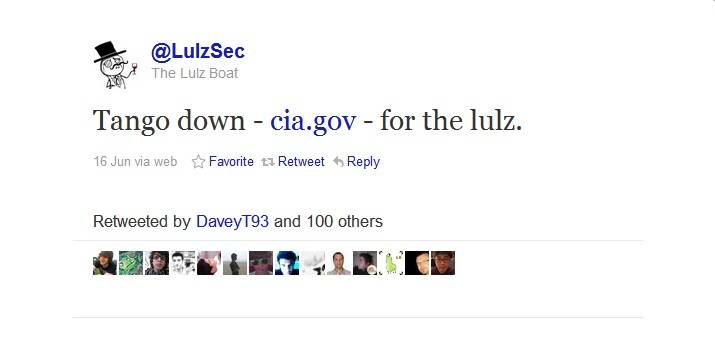
LulzSec Hackers are targeting CIA
The hacker group LulzSec has attacked once again. This time it wasn’t Sony, but the very same CIA website. According to a report by Reuters, this is the second time that the group hacks a government site. LulzSec made it public through their Twitter account that they were the ones […]